gactf 2020 writeup
考试考完,来吧咕咕咕掉的比赛重新写一下
re
checkin
ruby打包,直接定位createfile找到创建的文件
1 | |
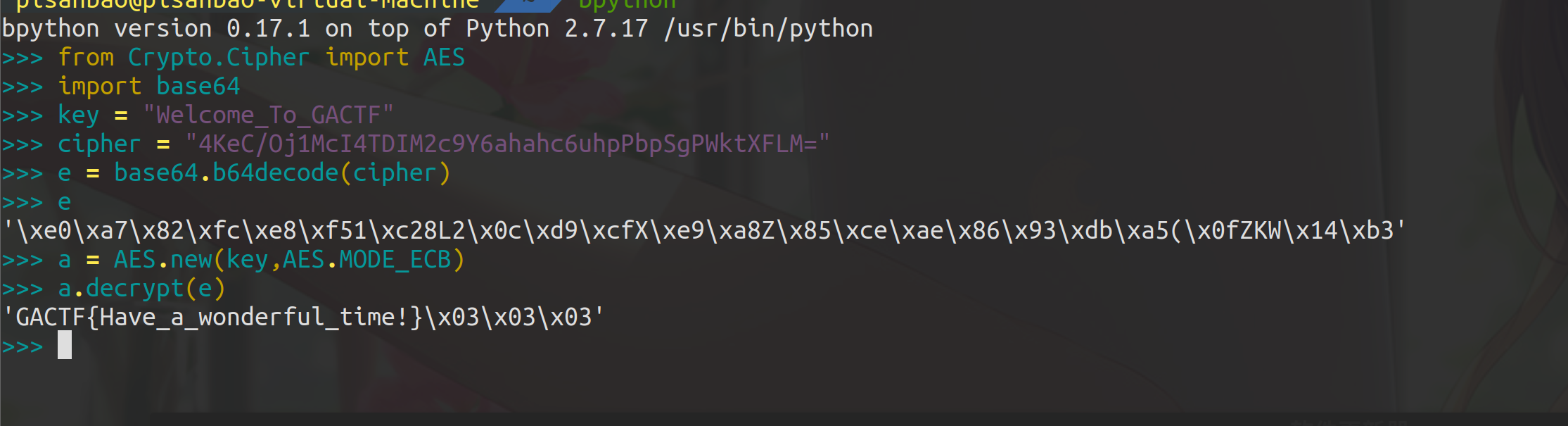
解密即可
WannaFlag
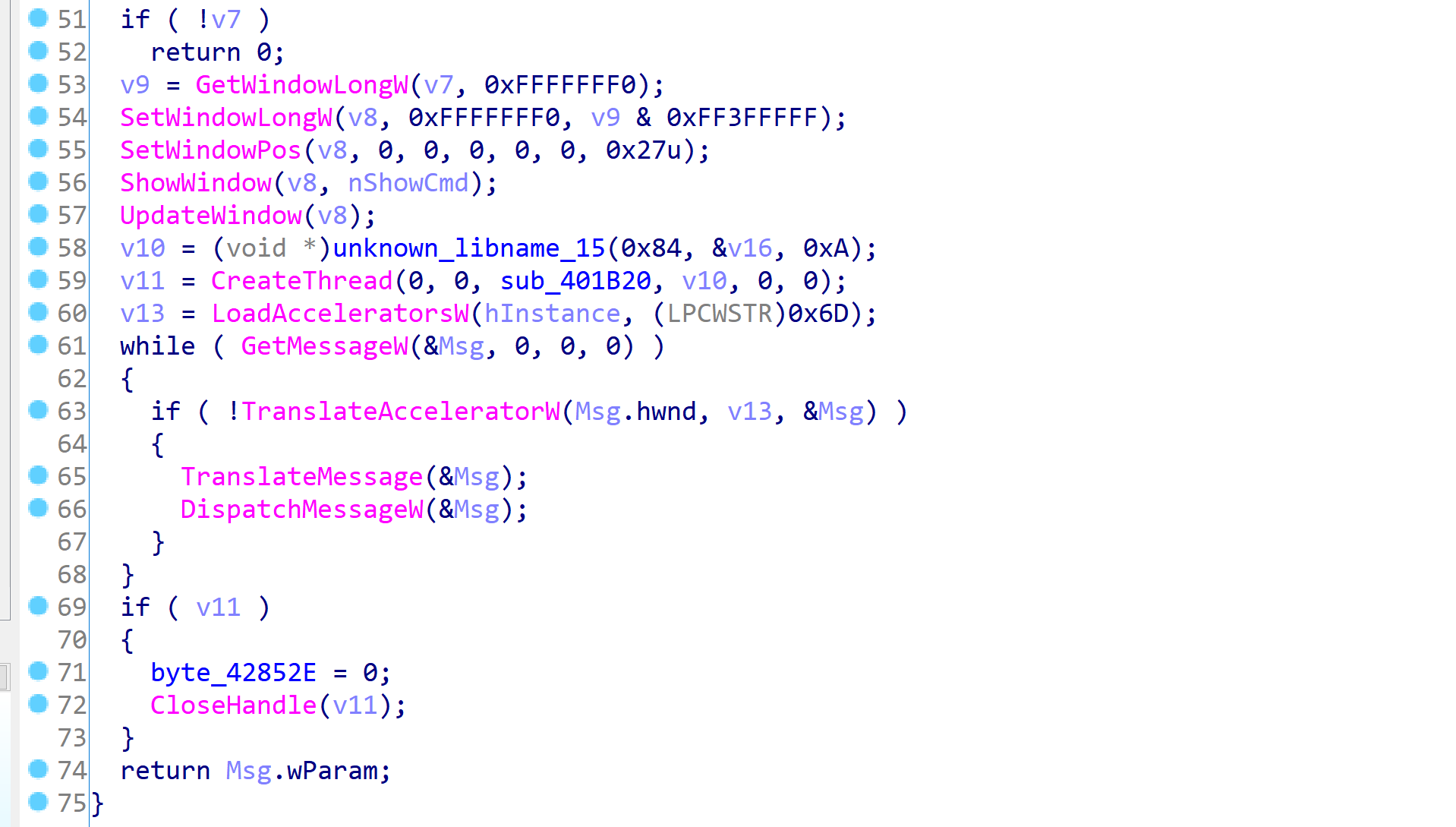
WINMAIN可以看到很明显的消息循环,向上面找一下能找到回调函数
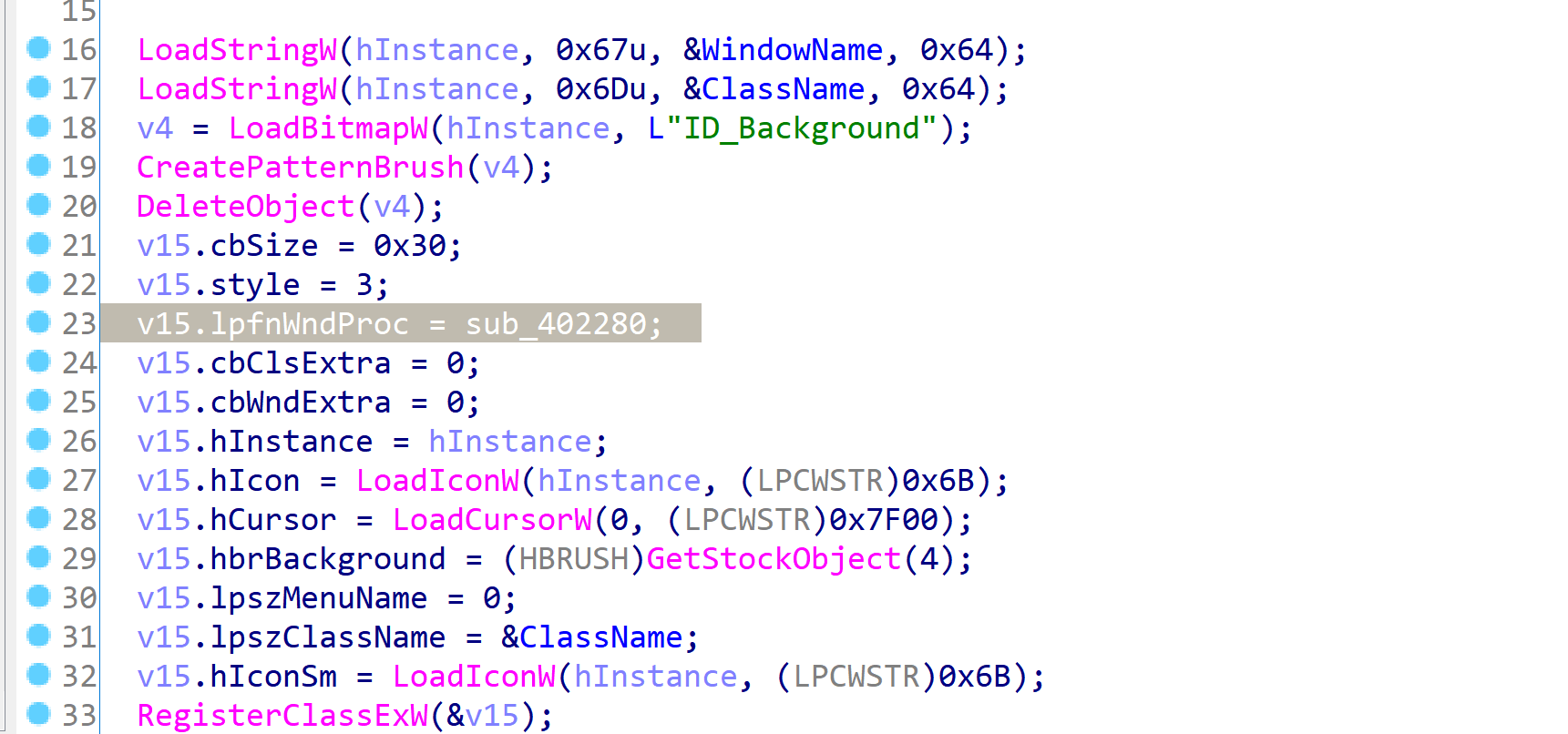
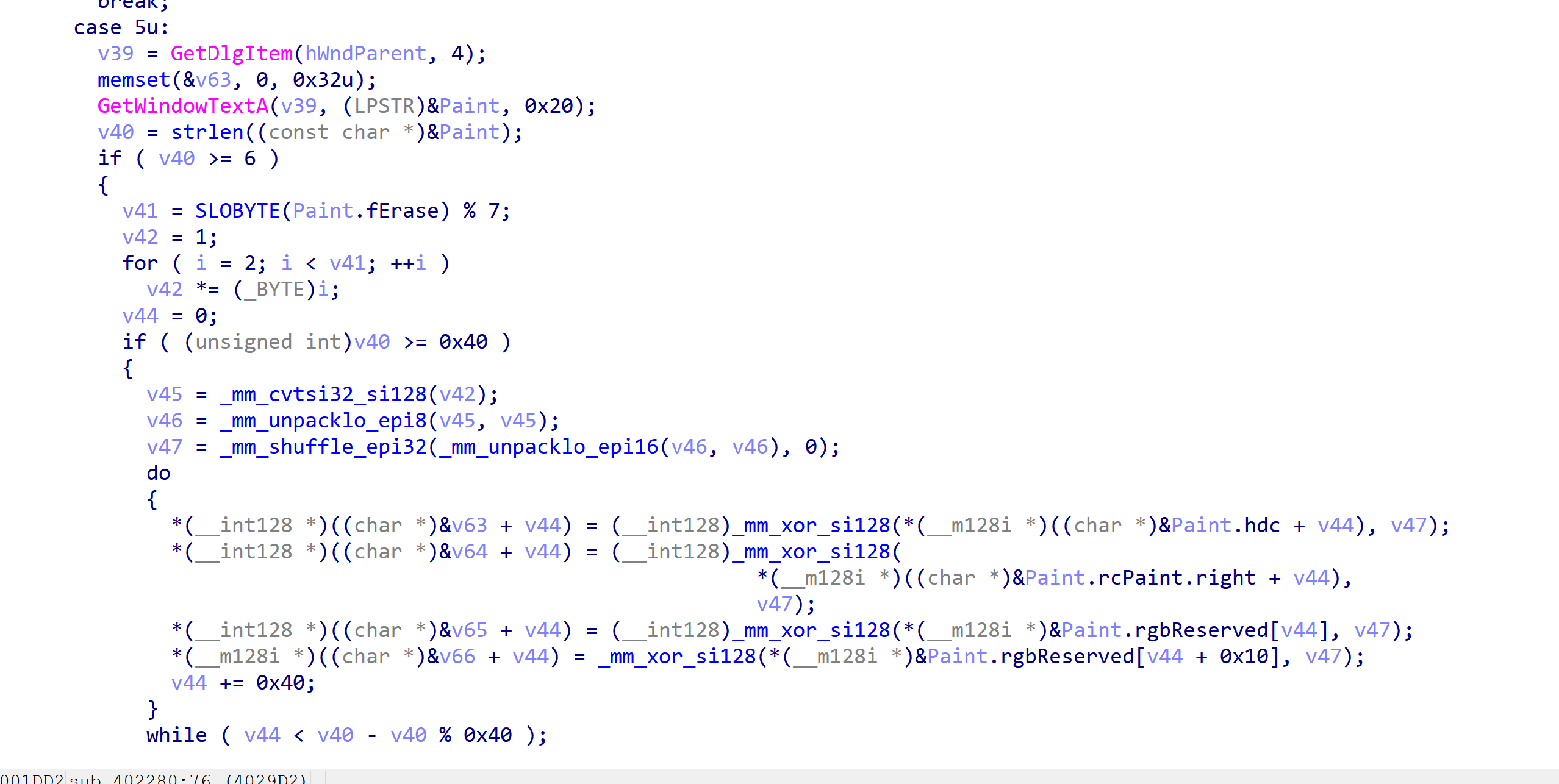
进去查看主要分析这个函数,录入key,加密后比较如果正确则弹msgbox然后解密flag
1 | |
加密部分不难
GACTF{WannaFlag_is_just_a_easy_re_with_a_beautiful_appearance}
EasyRe
先来个smc
然后是根据第一次输入的数据进行一次加密check,手动打log看
1 | |
弱智z3解出来是错的,这工具以后必卸,直接用c爆破出0xffe8bc9a,所以输入是4293442714
后面就是个xor
1 | |
Simulator
lc3汇编
用Simulate打开即可
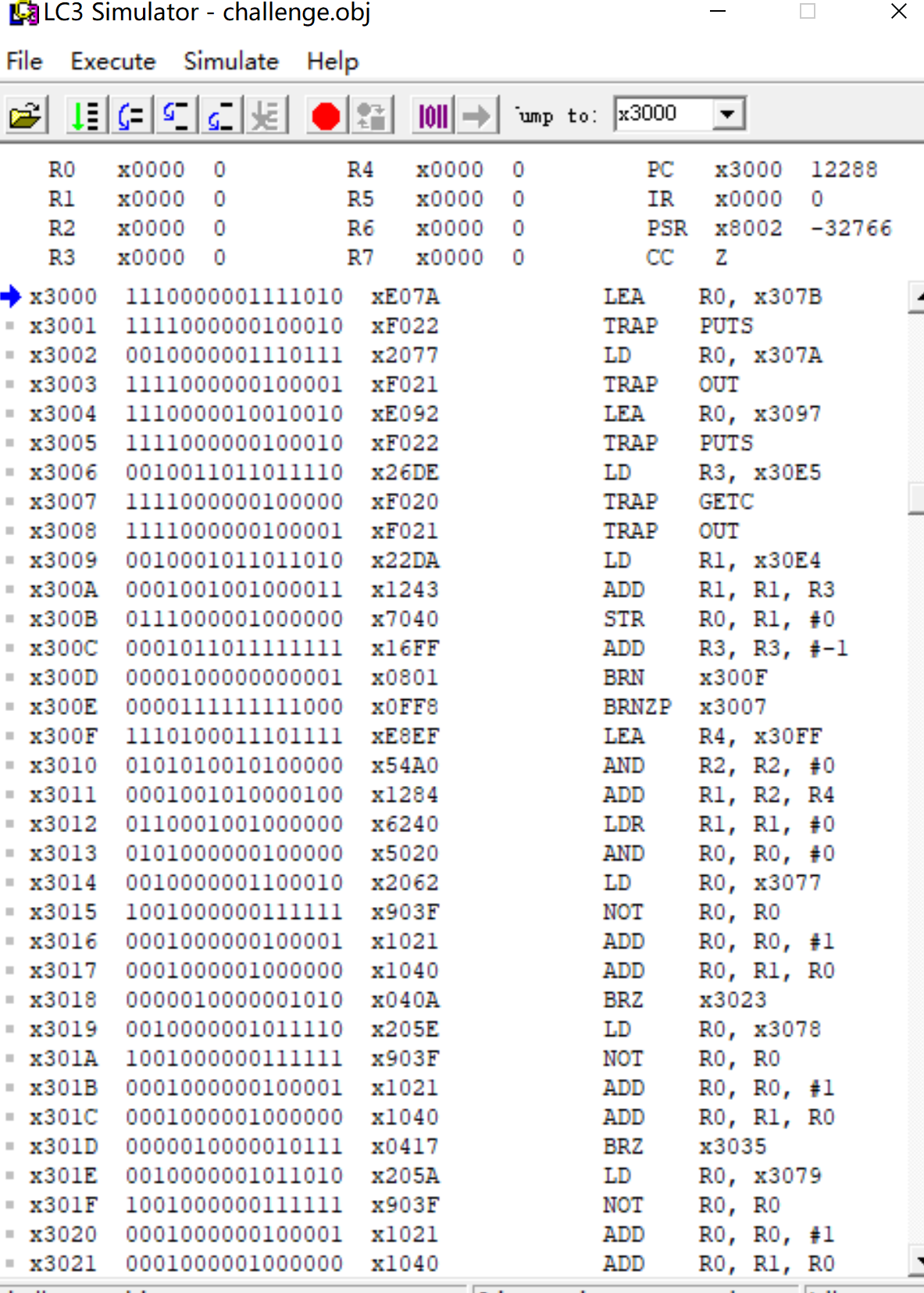
类似调试器,慢慢看,和mips有点像//考完计组后还没忘
前面就是疯狂录入到0x4000处
1 | |
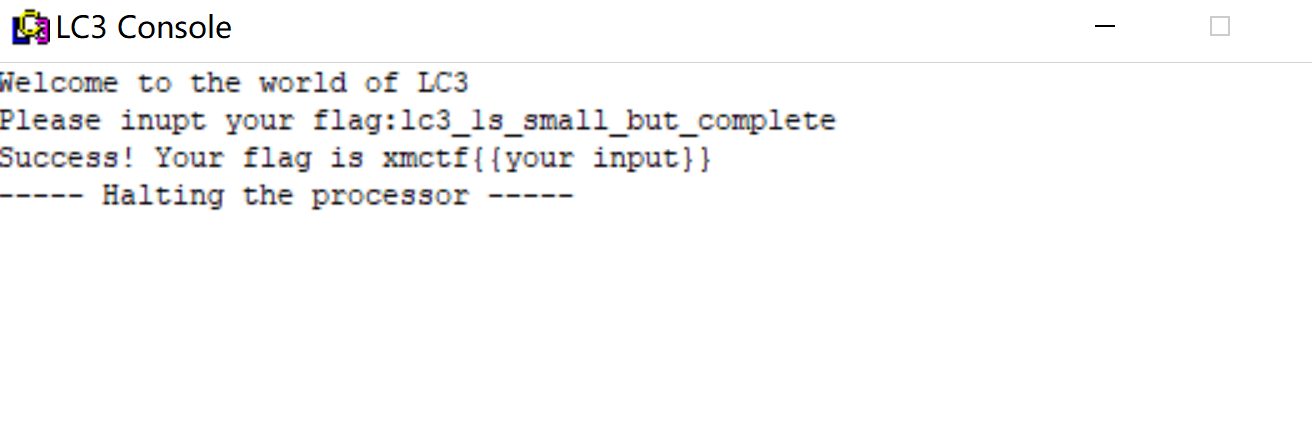
加密部分不难
PicCompress
一个图片压缩程序。。。一般情况下都不会去逆的,找一下源码
1 | |
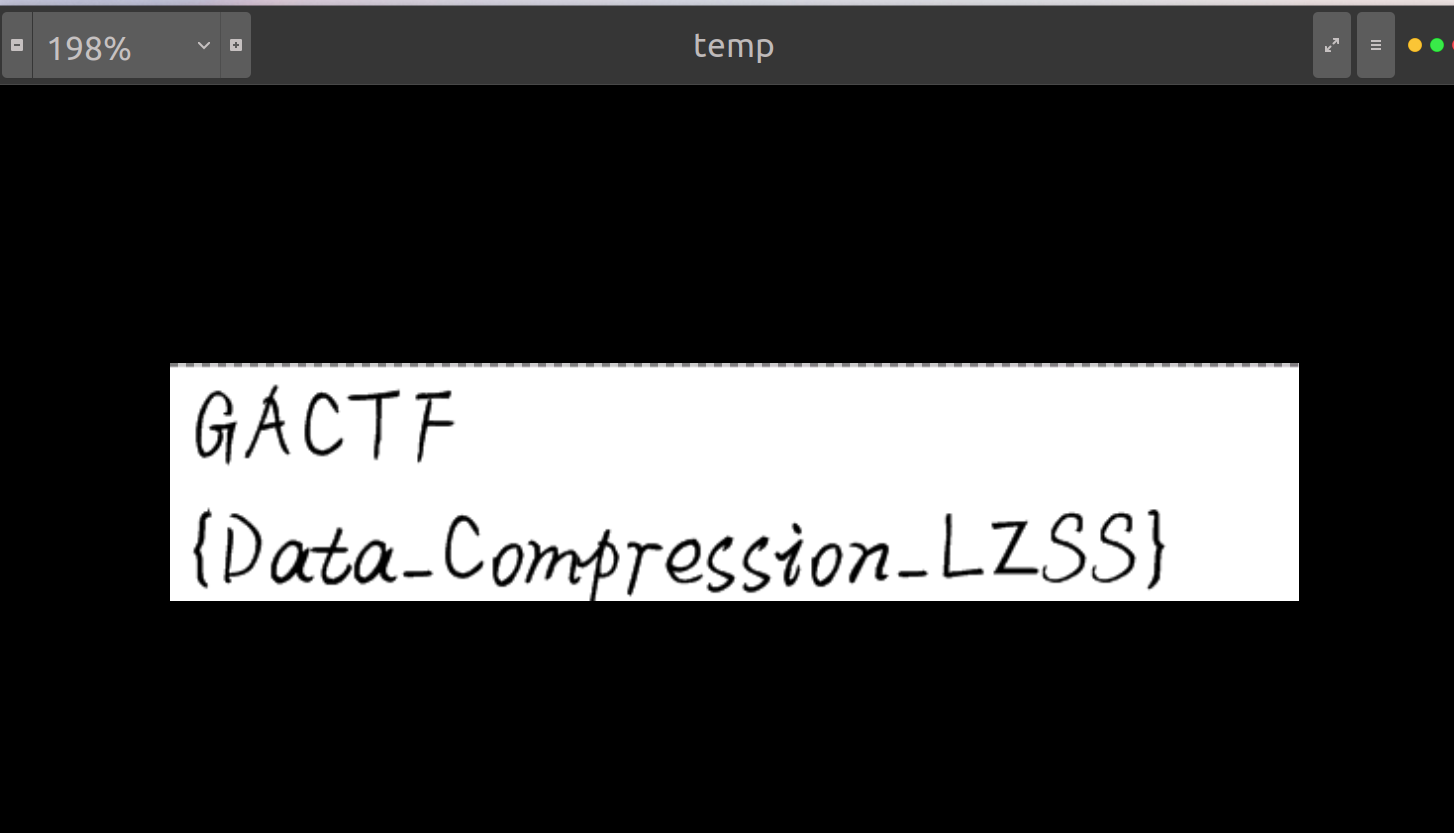
InfaintRe
静态编译,hint提示了可以搜索下
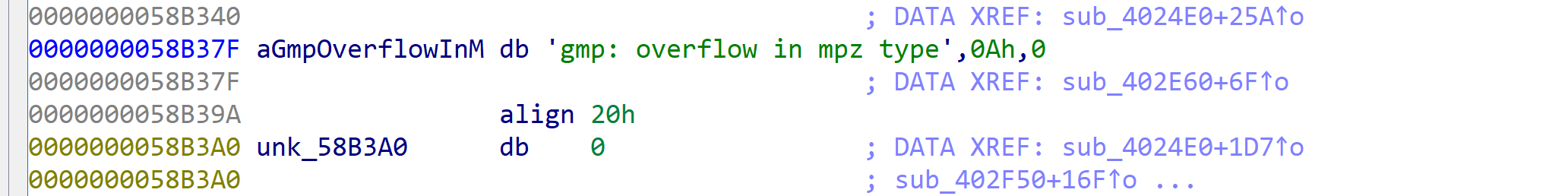
基本可以猜出gmp库
自己做签名文件试了下效果不咋地,只能识别出部分函数。。。
有些函数像mul因为有一点不同就没识别出
静态编译还是挺难受的
貌似是椭圆曲线。。。学完了再来看看把
gactf 2020 writeup
http://www.psbazx.com/2020/09/13/gactf-2020-writeup/